Generate Rsa Crypto Key Cisco Command
KB ID 0001322
- Cisco Crypto Key Generate Rsa Command For Ssh
- Crypto Key Generate Rsa Command Cisco Router
- Rsa Key Cisco Command
The label is important, I'll tell you! In a minute why C1801(config)# crypto key generate rsa modulus 1024 label C1801 The name for the keys will be: C1801% The key modulus size is 1024 bits% Generating 1024 bit RSA keys, keys will be non-exportable.OK C1801(config)#.Jan 6 15:22:25.339:%SSH-5-ENABLED: SSH 1.99 has been enabled! I don't recall a command that shows the crypto key bit size. You can view the configured key by issuing the 'show crypto key mypubkey rsa' command. If you are unsure about the size of the key you can always create a new one to the size that you want. Jun 11, 2019 SW1 ( config)# crypto key generate rsa. How many bits in the modulus 512: 1024% Generating 1024 bit RSA keys, keys will be non-exportableOK Set the size of key to 1024 bits. If your Cisco Switch is running an older version of Cisco IOS image, then it is extremely recommended that you upgrade to latest Cisco IOS.
Cisco Crypto Key Generate Rsa Command For Ssh

Crypto Key Generate Rsa Command Cisco Router
Now at command line you can fix this with a ‘Crypto Key Generate RSA Modulus 2048‘ command, but you can’t get to command line only ASDM. On older versions of the ASDM you could generate the keypair in the Identification Certificates section (well you still can but only if you are also generating a certificate request file). May 20, 2014 Author, teacher, and talk show host Robert McMillen shows you how to use the Cisco ASA version 9 generate RSA keys command. Jan 14, 2019 Symptom: If you configure the crypto key generate rsa command on a Cisco uBR10K CMTS with dual performance routing engines (PREs), the command fails to synchronize to the secondary PRE.
Problem
Rsa Key Cisco Command
I’ve lost count of the number of times this has happened to me! Most of my colleagues prefer to use the ASDM for remote management, but if (like me) you work at command line, then sometimes people <ahem> forget to generate the RSA keypair when deploying a firewall. Then even if SSH access and AAA is setup correctly, you still can’t get in via SSH. Instead you see the following;
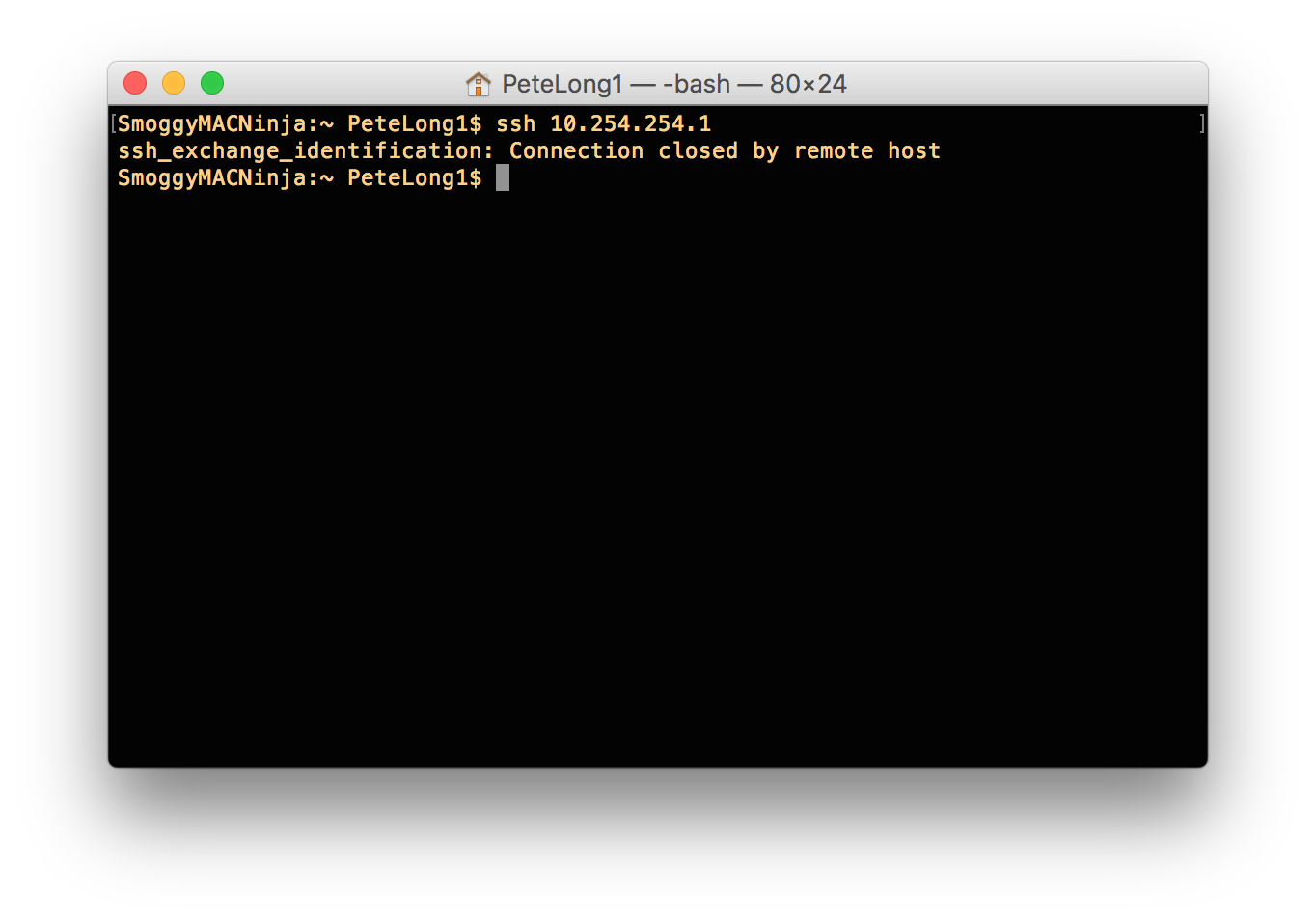
RoyalTS and RoyalTSX: ssh_exchange_identification: Connection closed by remote host.
PuTTY: PuTTY Fatal Error: Server unexpectedly closed network connection.
SecureCRT: Connection closed.
OSX/Linux: ssh_exchange_identification: Connection closed by remote host.
Now at command line you can fix this with a ‘Crypto Key Generate RSA Modulus 2048‘ command, but you can’t get to command line only ASDM.
Solution
On older versions of the ASDM you could generate the keypair in the Identification Certificates section (well you still can but only if you are also generating a certificate request file). So, as we are command line warriors, lets use the ASDM’s command line!
Tools > Command Line Interface > Multiple Line
Send > Wait a couple of minutes and try again.
REMEMBER: I’m assuming you have SSH setup correctly if not, see the following article;
Related Articles, References, Credits, or External Links
NA /product-key-office-professional-plus-2010-generator.html.