Generate Jwt Secret Key C
- Generate Jwt Secret Key C Sheet Music
- Generate Jwt Secret Key C#
- Secret Key Platinum
- Generate Jwt Secret Key Card
- Generate Jwt Secret Key
- Secret Key Skin Care
- Generate Jwt Secret Key C Key
TOP(jsrsasign) WIKI DOWNLOADS TUTORIALS API REFERENCE DEMOS
To use jsrsasign including jsjws on your browser, just include 'jsrsasign-latest-all-min.js' script as following: /office-2000-product-key-generator.html.
JSON Web Token(JWT) generation is very similar to JSON Web Signature(JWS) generation since those difference is just payload. JWS generation is to create header and payload JSON object with necessary claims and then sign it.
Drag the Generate JWT action onto the processing flow line after the set-variable icon. A configuration panel automatically opens. Enter request.headers.iss-claim in the Issuer Claim field. Enter request.headers.aud-claim in the Audience Claim field. Enter hs256-key in the Sign JWK variable name field. Select HS256 in the Cryptogrpahic. The signing key is a byte array of any value or length you wish. Most JWT libraries allow you to use any string as key, which is converted to byte array. To generate a secure 20 byte key, bs64 encoded. Dd if=/dev/random bs=20 count=1 status=none base64. Aug 31, 2017 JWT (JSON Web Tokens) is open, security protocol for securely exchanging claims between 2 parties. A server generates or issues a token and is signed by a secret key. The client also knows the secret key and the key and can verify if the token is genuine. The token contains claims for authentication and authorization. This lets you put non-convential JWT data in here in the format you desire. // DO NOT ABUSE IT! If your tokens get too fat you aren't using them as intended (as identity). You // will only hurt yourself in the long run. (C) Create JWT Using HS256, HS384, or HS512. Demonstrates how to create a JWT using HS256, HS384, or HS512. (HS256 is JWT's acronym for HMAC-SHA256.) When HMAC is used, the secret is a shared secret (i.e. Password) that both client and server know beforehand. This example also demonstrates how to include time constraints: nbf: Not Before Time.
Time in JWS/JWT, integer value for UNIX origin time since 1970 Jan 1 will be used. To specify time value KJUR.jws.IntData.get method is very useful.
Here is a sample for a JWT generation with HS256 signature algorithm:
When you want to sign JWT by your private key of public key cryptography, KEYUTIL.getKey method can be used to load PKCS#1 or PKCS#8 PEM formatted encrypted or plain private key. Here is an example:
Please also see Online JWT generation/verification tool.
jwt.io site interoperability
jwt.io site can generate and verify HS256/384/512 JWT online and it uses old version of jsrsasign.However difference of way to specify password between jwt.io and jsrsasign may make some confusion.
jwt.io
- default password is an ascii string of 'secret'.
- it can accept password ascii string or Base64URL encoded data.
jsrsasign
- Password encoding is detected automatically by default. If is hexadecimal string, then decode it as hexadecimal.
- It supports many way of password encoding: raw string, utf8 string, hexadecimal string, base64 string, base64url string.
In order to verify jsrsasign generated HS* JWT by jwt.io site, specify password as one of follows:
Pseudocode:
The steps called out here should work on a Mac as well. The only thing that might be different is the sed command used below. Instead of using -E, you will have to use -r to run sed with extended regular expression support
Use data from this tutorial:
Header:
Base64 Encode of Header:
echo -n '{'alg':'HS256','typ':'JWT'}' openssl base64 -e -A
OR Generate rsa ssh key mac.
echo -n '{'alg':'HS256','typ':'JWT'}' base64
Generate Jwt Secret Key C Sheet Music
Output: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
However, we need Base64 URL encoding of the Header.
Base64 URL Encoding of Header:
echo -n '{'alg':'HS256','typ':'JWT”}' openssl base64 -e -A sed s/+/-/ sed -E s/=+$//
OR
echo -n '{'alg':'HS256','typ':'JWT”}' base64 sed s/+/-/ sed -E s/=+$//
Output: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
Generate Jwt Secret Key C#
Repeat the same series of steps for Payload.
Payload:
Base64 Encoding of Payload:
echo -n '{'iss':'cisco.com','exp':1470839345,'name':'Anand Sharma','cda-admin':true}' openssl base64 -e -A
OR
echo -n '{'iss':'cisco.com','exp':1470839345,'name':'Anand Sharma','cda-admin':true}' base64
Output: eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9
Base64 URL Encoding of Payload:
echo -n '{'iss':'cisco.com','exp':1470839345,'name':'Anand Sharma','cda-admin':true}' openssl base64 -e -A sed s/+/-/ sed -E s/=+$//
OR
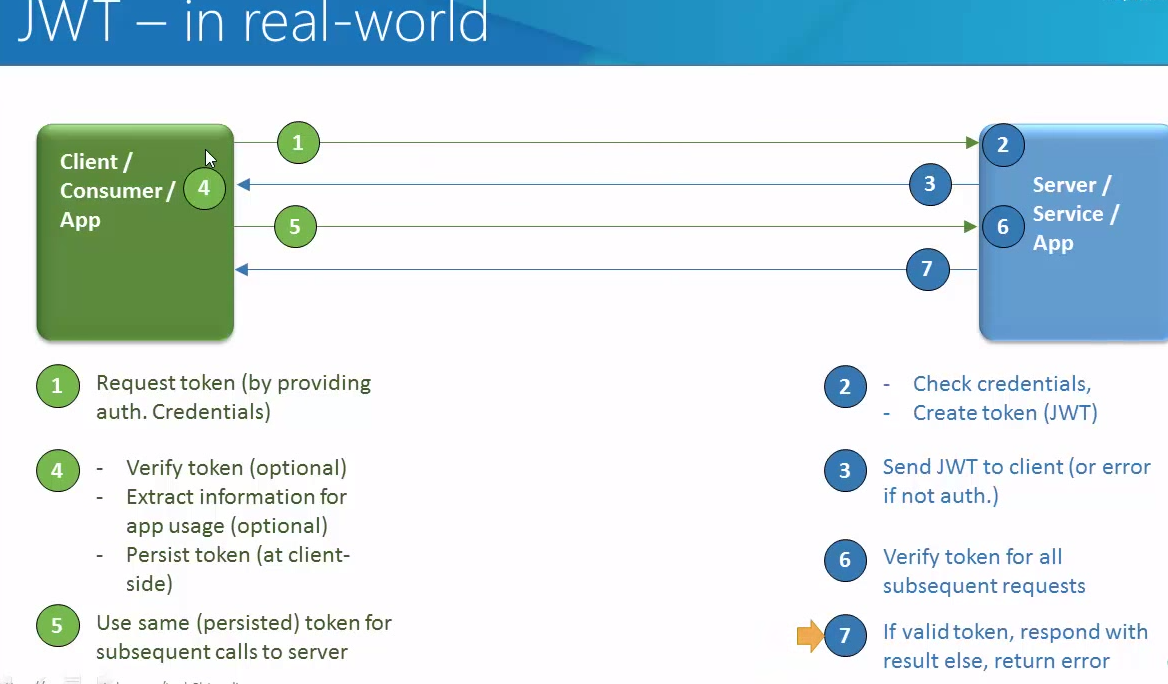
Secret Key Platinum
echo -n '{'iss':'cisco.com','exp':1470839345,'name':'Anand Sharma','cda-admin':true}' base64 sed s/+/-/ sed -E s/=+$//
Generate Jwt Secret Key Card
Output: eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9
###Y:eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9
###HMAC SHA256 Digest (Default output in Hex):echo -n 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9' openssl dgst -sha256 -hmac secret
Output: 21557ae7825781d1176595f7ce506b96e3e02fc0711564d02abb4722c3be5eb5
This is where the problem starts. What we forget is that the openssl dgst command is dumping the hexadecimal encoded version of the digest, which is really a binary data. So if you pass this value (the hexadecimal output shown above) to the base64 encoding command, you will get Base64 encoding of basically 'plain text data”. Why? Because it is going to treat the hexadecimal output as plain text (or string). What we need is to feed the binary data into base64 encoding command. Btw, this StackOverflow question and answer was the thing that really helped me out. Plus, the Swiss Converter Tool allowed me to actually confirm that my understanding was correct
Base64 URL Encode the HMAC SHA256 Digest (Output in Binary):
echo -n 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9’ openssl dgst -sha256 -hmac secret -binary openssl base64 -e -A sed s/+/-/ sed -E s/=+$//
Generate Jwt Secret Key
Output: IVV654JXgdEXZZX3zlBrluPgL8BxFWTQKrtHIsO-XrU
Secret Key Skin Care
JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjaXNjby5jb20iLCJleHAiOjE0NzA4MzkzNDUsIm5hbWUiOiJBbmFuZCBTaGFybWEiLCJjZGEtYWRtaW4iOnRydWV9.IVV654JXgdEXZZX3zlBrluPgL8BxFWTQKrtHIsO-XrU
Go to jwt.io and verify the JWT token, including the signature.
Generate Jwt Secret Key C Key
Yippie!