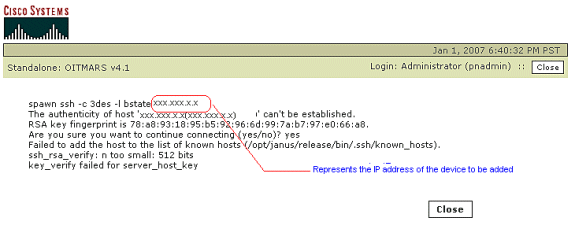
Asa 5505 Attempt To Generate Rsa Keys Failed
- To generate a Certificate Signing Request (CSR) for Cisco ASA 5510, a key pair must be created for the server. These two items are a public key and a private key pair and cannot be separated. Like all key pairs the private key once created will remain on the system where the CSR is made.
- May 21, 2014 Author, teacher, and talk show host Robert McMillen shows you how to use the Cisco ASA version 9 generate RSA keys command. Author, teacher, and talk show host Robert McMillen shows you how to.
Crypto key generate rsa general-keys modulus 4096. Failing that try rebooting the ASA. Failing that, make sure you are using an up to date version of PuTTY, and enable stronger keys on the ASA with (your software might be too old for this): sh key-exchange group dh-group14-sha1. Jan 09, 2010 Author and talk show host Robert McMillen explains the generate RSA keys command for a Cisco ASA or Pix. This How To Video also as audio instruction. Cisco ASA ver. 6, 7, and 8.2: Generate RSA.
Zeroize the key:
ciscoasa(config)# crypto key zeroize rsa
WARNING: All RSA keys will be removed.
WARNING: All device digital certificates issued using these keys will also be removed
Do you really want to remove these keys? [yes/no]: y
ciscoasa(config)#
Generating RSA key needs to define a domain name, this is the same as in IOS. download instructions for kodi 17
ciscoasa(config)# domain-name cyruslab.com
ciscoasa(config)#
Generate a 1024-bit long RSA key:
ciscoasa(config)# crypto key generate rsa general-keys modulus 1024
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait…
ciscoasa(config)#
Actually it is sufficient if I just type crypto key generate rsa <cr>, the interactive prompt will just prompt me for the length of the key (modulus).
This is the 1024-bit long RSA key which I have just generated:
ciscoasa(config)# sh crypto key mypubkey rsa
Key pair was generated at: 06:20:15 UTC Apr 8 2010
Key name: <Default-RSA-Key>
Usage: General Purpose Key
Modulus Size (bits): 1024
Key Data:
30819f30 0d06092a 864886f7 0d010101 05000381 8d003081 89028181 00c2890c
ad9065a0 f17eebbd 726029dc 0a9f40a9 ca714031 5de9d15b fe7b8fc7 e11e7ffd
8f27befc beaf0aae fa937c69 482a1595 f8865cc1 d8ced14a 737243c3 8f9886ab
75be998a 8a7437a1 bac57f34 d31774b7 a53cd803 a7837bc4 92f9f326 8fc818a5
54ca0476 3c864534 7b50d635 88905d28 cfeec63d e32324a9 98eba845 3b020301 0001
Allow ssh connection from my private network:
ciscoasa(config)# ssh 192.168.1.0 255.255.255.0 inside
Asa 5505 Attempt To Generate Rsa Keys Failed To Start
Allow ssh connection from the internet (any connection):
ciscoasa(config)# ssh 0 0 outside
Set up ssh idle time-out period (maximum is 1hour):
ciscoasa(config)# ssh timeout 30
ssh has two versions: 1 and 2. /call-of-duty-black-ops-2-steam-key-generator-v13exe.html. ssh version 1 is less secured than version 2. My default ssh supports two versions:
ciscoasa(config)# sh ssh
Timeout: 30 minutes
Versions allowed: 1 and 2
192.168.1.0 255.255.255.0 inside
0.0.0.0 0.0.0.0 outside
To support only version 2, I have to explicitly tell my firewall with this command:
ciscoasa(config)# ssh version 2
ciscoasa(config)# sh ssh
Timeout: 30 minutes
Version allowed: 2
192.168.1.0 255.255.255.0 inside
0.0.0.0 0.0.0.0 outside
I think putty supports ssh version 2. so I shall test it…
Click yes button to store this key into my windows XP.
Great! Putty supports ssh version 2.
From my console, I can check the current ssh sessions to my ASA5505:
To kill ssh session:
ssh disconnect <sid> for disconnecting ssh session.kill <sid> for killing telnet session.

LOL! SSH session has been sniped!
Asa 5505 Attempt To Generate Rsa Keys Failed Update
Welcome back to this series where we cover CCNA Security topics using Cisco Packet Tracer in our labs. In the previous lab, we started looking at the Cisco ASA and we will continue looking at this Cisco appliance in this lab.
The lab setup from the last article is as shown below:
In this lab, we will configure routing on the Cisco ASA, look at the Cisco Modular Policy Framework (MPF) and also configure SSH for management access to the Cisco ASA.
Two files are attached to this article:
- cisco_asa_routing_mpf_mgt_init.pkt: This Packet Tracer file is actually the “final” PKT file from the previous lab.
- cisco_asa_routing_mpf_mgt_final.pkt: This Packet Tracer file contains the lab setup with the ASA fully configured to meet the lab requirements.
The tasks for this lab are as follows:
- Configure a loopback interface on the Outside_RTR with an IP address of 8.8.8.8/32.
- Configure a default route on the ASA pointing to the Outside_RTR. Ensure that you can ping the newly configured loopback on the Outside_RTR from the Cisco ASA.
- The ‘Inside User’ should be able to initiate connections to the ‘Web Server’ and get a response. You should also ensure that ping from the ‘Inside User’ to the ‘Web Server’ is successful. Do not use an access list to accomplish this.
- Enable SSH access to the ASA from any IP address on both the inside and outside interfaces. Create a local user on the ASA to be used for authentication with the following credentials: Username – “insideuser” and Password – “userpwd”.
Lab Solutions
Task 1: Loopback Interface Settings
The goal of this task is just to simulate an external host, e.g. a device on the Internet.
Task 2: Default Routing
As I said in the last article, many commands that have “ip” in the Cisco IOS do not have “ip” in the Cisco ASA. The route command, used to configure static/default routes on the Cisco ASA, is an example of this.
Another thing to keep in mind with the Cisco ASA is that you must specify an interface name (e.g. inside, outside) for any route statement. This interface name specifies the interface through which the next hop IP address is reachable.
Finally, instead of specifying “0.0.0.0 0.0.0.0” like we do on the Cisco IOS, we can shorten it to “0 0” on the Cisco ASA. However, this short form is not (yet) implemented in Packet Tracer so we must specify it in its full form.
To test this configuration, we will ping the 8.8.8.8 IP address from the Cisco ASA:
Task 3: Inside to DMZ Communication
In the last lab, we said that due to the license that comes with the Cisco ASA in Packet Tracer (Base License), the 3rd VLAN we created (dmz) will be a restricted VLAN, i.e. it will only be able to initiate a connection to only one other VLAN. In that lab, we restricted the dmz VLAN from initiating a connection to the inside VLAN. Notice the word “initiate” in that sentence? Free windows 7 enterprise activation key generator. It means that even though the dmz VLAN cannot initiate traffic to the inside, the inside VLAN can actually initiate traffic to the dmz and the dmz will respond.
Since the inside interface is on a higher security interface than the dmz, traffic from the inside to the dmz will be allowed by default. We can confirm this by opening an HTTPS connection from the ‘Inside User’ to the ‘Web Server’:
Note: Even though HTTP is also enabled on the Web Server, http://172.16.10.100 doesn’t work for some reason. I assume it’s some limitation with Packet Tracer. Two services I found to work are HTTPS and SMTP.
However, the task also requires that ping traffic from the ‘Inside User’ to the ‘Web Server’ is successful, so let’s test that:
As you can see, the ping failed. The problem is that, by default, ICMP inspection is not enabled on the Cisco ASA so even though the ping from the inside is getting to the dmz, the return traffic is not permitted. There are two ways around this issue:
- Use the Cisco Modular Policy Framework (MPF).
The task specifically said not to use an ACL so we are left with the second option. Although you can configure an ICMP policy on the ASA, an easier option is to copy the default MPF configuration from the Cisco site and edit it to include ICMP inspection. Due to the limitations of Packet Tracer, some of the commands included in the default MPF configuration are not supported so you will end up with a configuration similar to the following:
As you can see, I have enabled ICMP inspection (inspect icmp) under the “global_policy” policy map. Let’s test again:
Task 4: SSH Access
To enable SSH on the Cisco ASA, there are a couple of things we need to do:
- Generate an RSA Key Pair. There is a default RSA Key pair on the Cisco ASA called “Default-RSA-Key”.
- If you will be using local authentication, create username/password combinations.
- Configure the ASA to use local authentication for SSH connections.
- Specify what IP addresses can manage the ASA using SSH and through what interface.
We can view the default RSA key pair using the show crypto key mypubkey rsa command:
The other necessary configuration is as follows:
Let’s first test this configuration from the ‘Inside User’ by opening command prompt and typing “ssh –l insideuser 10.0.0.1”:
The SSH connection was successful. Let’s now test from the Outside_RTR:
Great! We have now successfully completed the tasks in this lab.
Summary
This brings us to the end of this Packet Tracer lab where we have configured routing, Cisco MPF and also enabled SSH on the Cisco ASA 5505.
In the next article, we will continue with another lab on the Cisco ASA. I hope you have found this lab insightful.
Asa 5505 Attempt To Generate Rsa Keys Failed Update
References and Further Reading
Asa 5505 Attempt To Generate Rsa Keys Failed To Work
- CCNA Security Certification Series- #3 Cisco Firewall Technologies- cont’d: http://resources.intenseschool.com/ccna-security-certification-series-3-cisco-firewall-technologies-contd/
- CCNA Security Certification Series – #4 Cisco Firewall Technologies – cont’d: http://resources.intenseschool.com/ccna-security-certification-series-4-cisco-firewall-technologies-contd/